Infrastructure as Code (IaC) Part 4: Advanced best practices
Introduction
Infrastructure as Code (IaC) has evolved beyond basic automation to encompass sophisticated practices that ensure scalability, reliability, and maintainability. Three key advanced practices stand out for organizations looking to elevate their IaC implementation: modular infrastructure design, automated testing, and robust state management. Through modular design, teams can create reusable components that promote consistency across different environments while reducing code duplication. Automated testing frameworks help validate infrastructure configurations before deployment, catching potential issues early in the development cycle. Meanwhile, proper state management using remote backends ensures secure collaboration and prevents concurrent modification conflicts. These practices form the foundation of a mature IaC implementation that can support enterprise-scale infrastructure needs.
Modular Infrastructure Design
Modular infrastructure design represents a cornerstone of Infrastructure as Code (IaC) implementations. Beyond basic modularization, one should implement a hierarchical module structure that separates concerns across logical boundaries while maintaining clear interfaces between components.
The most sophisticated modular designs implement the principle of “loose coupling and high cohesion”. Modules should perform distinct functions with minimal dependencies on other modules. This approach enables teams to evolve individual infrastructure components independently without cascading changes throughout the codebase. Organizations implementing this pattern typically develop three distinct module layers:
- Foundation modules that establish core networking, security boundaries, and shared services.
- Service modules that deploy application-specific infrastructure with standardized interfaces.
- Orchestration modules that compose these components together for specific environments.
Let’s examine a comprehensive example using Terraform:
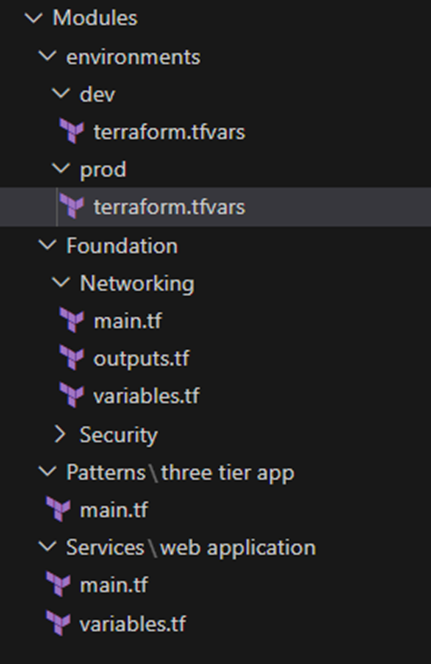
This is an example of the file structure that can be used to follow the best practice of Hierarchical Module Organization
- Foundation layer (Networking module)
- Defines VPC, subnets, and security groups
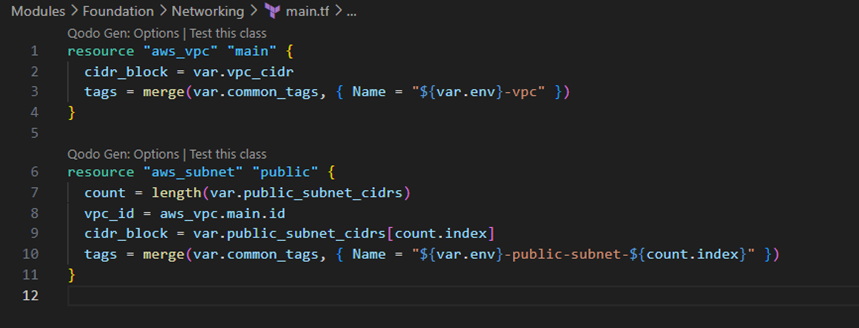
- Main.tf:
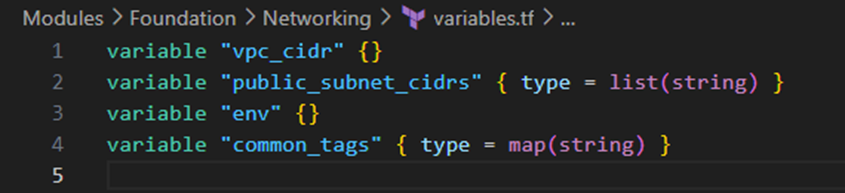
- Variables.tf:
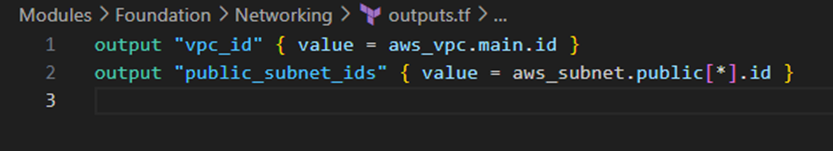
- Outputs.tf:
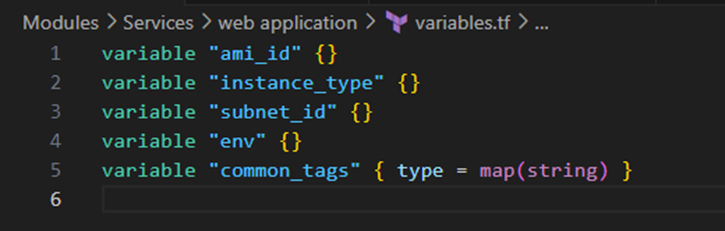
- Service Layer (web application module)
- Uses networking outputs without modifying them (Composition over Inheritance).
- Main.tf:
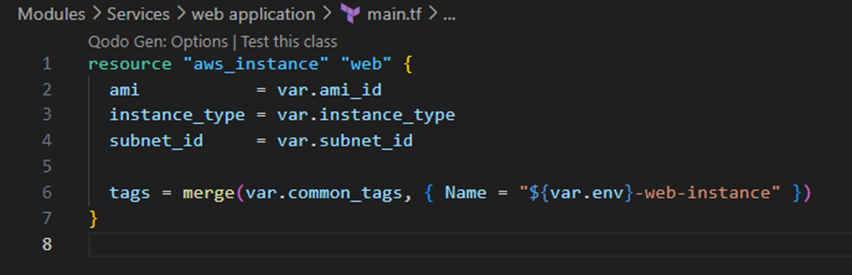
- Variables.tf:
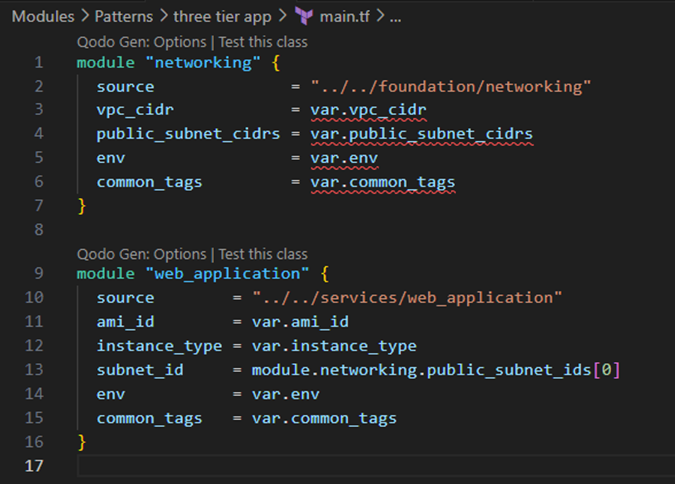
- Pattern layer (three tier app module)
- Combines foundation and service modules into a reusable pattern.
- Main.tf:
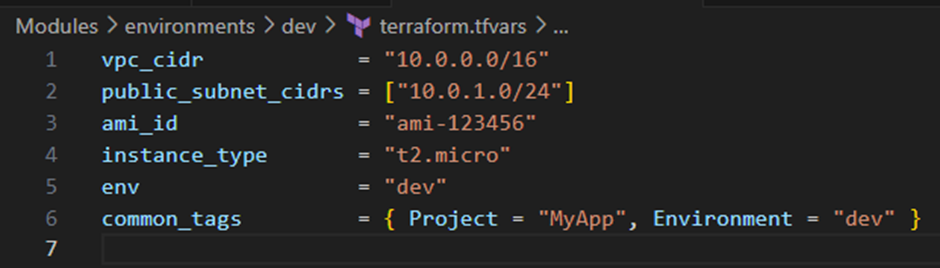
- Environment specific config
- Separate configuration for different environments
- Dev/terraform.tfvars:
- Prod/terraform.tfvars:
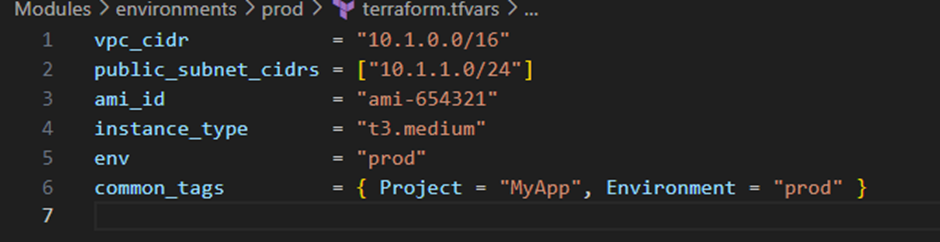
Hierarchical Module Organization – The structure implements three distinct layers – foundation modules (networking, security), service modules (web application), and orchestration modules (three tier app pattern). This separation allows specialized teams to focus on their areas of expertise while maintaining a consistent approach across the organization.
Interface Contracts: Each module explicitly defines its inputs (variables.tf) and outputs (outputs.tf), creating clear contracts between modules. This approach supports the principle of information hiding – consumers of a module don’t need to understand its internal implementation details.
Composition Over Inheritance: The pattern module doesn’t extend or modify the foundation modules; it composes them together. This composition-based approach provides flexibility to reorganize infrastructure components without altering their implementation.
Environment-Specific Configuration: The environment directories contain only the configuration values specific to each deployment context. This separates the “what” (infrastructure patterns) from the “where” (environment-specific settings), enabling consistent infrastructure across environments.
Standardized Resource Tagging: The example includes a comprehensive tagging strategy that propagates tags from higher-level modules down to individual resources, enabling consistent governance and cost allocation.
Automated Testing
Mature Infrastructure as Code (IaC) implementations require robust automated testing strategies that extend beyond basic validation. Advanced best practices suggest that one should implement multi-layered testing approaches that validate infrastructure at multiple stages of the deployment pipeline. This comprehensive testing methodology begins with static analysis, which examines code without execution, progresses through unit testing of individual modules, and culminates in integration testing across interconnected resources.
Organizations implementing advanced IaC testing practices adopt a “shift-left” security mindset, where security validation occurs early in the development lifecycle rather than as an afterthought. This approach integrates policy-as-code frameworks that collate compliance requirements directly into testing suites, ensuring that infrastructure meets organizational and regulatory standards before deployment. The most sophisticated implementations maintain separate testing environments that closely mirror production, allowing teams to validate complex infrastructure changes in isolation before affecting critical systems.
Let’s examine a practical example using Terraform and Terratest, a Go library that simplifies testing for Terraform code:

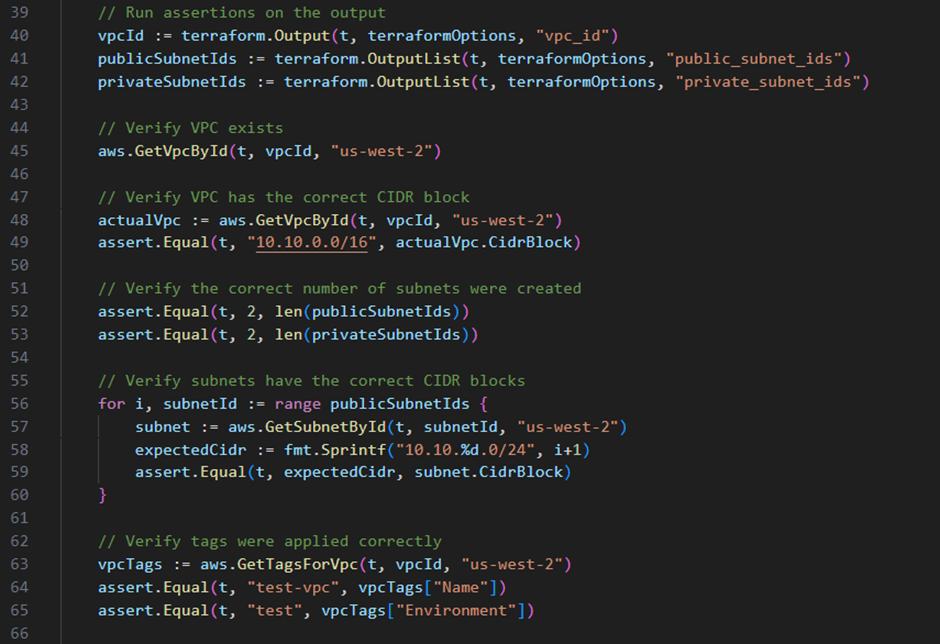
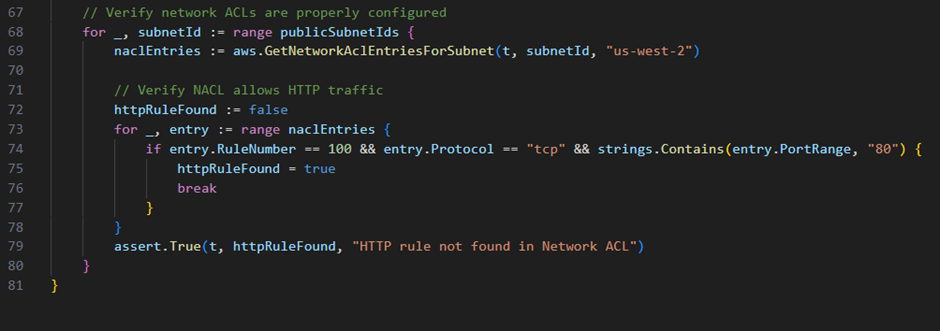
This testing approach illustrates several advanced IaC testing principles. First, it implements a complete test lifecycle – provisioning actual infrastructure, validating its properties, and then destroying it to prevent lingering resources. The test verifies not only the basic existence of resources, but also validates specific configurations such as CIDR blocks, subnet relationships, and security controls through network ACL rules.
Beyond this example, enterprise-grade IaC testing integrates with CI/CD pipelines to provide automatic quality gates. When developers submit infrastructure changes, these pipelines automatically execute tests to verify compliance with organizational standards. Advanced implementations maintain “golden state” snapshots that detect drift between planned and actual infrastructure configurations, ensuring that out-of-band changes don’t compromise security or reliability.
Most importantly, comprehensive testing frameworks validate functional requirements beyond just resource creation. They verify that applications can actually operate on the infrastructure, testing connectivity between components, failover capabilities, and performance under load. By treating infrastructure code with the same rigor as application code, organizations can achieve higher reliability while still moving quickly to meet business needs.
State Management
Effective state management represents one of the most critical aspects of mature Infrastructure as Code implementations. Beyond basic remote storage, advanced practitioners implement state file segmentation strategies that partition infrastructure state across logical boundaries. This approach ensures that errors in one infrastructure component don’t affect others. Organizations typically segment state files according to environment boundaries (production vs. development), resource lifecycles (long-lived network infrastructure vs. ephemeral compute resources), or team ownership boundaries to enable parallel workflows.
Sophisticated IaC implementations leverage state file encryption at rest and in transit, often implementing additional access controls beyond what the native backend provides. Advanced teams create structured workflows for state file operations like import, move, and removal that require peer review and audit trails. These workflows treat state manipulation as a potentially dangerous operation that warrants the same level of scrutiny as production infrastructure changes themselves. The most mature implementations maintain point-in-time state file backups to enable disaster recovery scenarios beyond what version control provides.
Let’s examine a configuration example for an advanced Terraform remote state implementation:
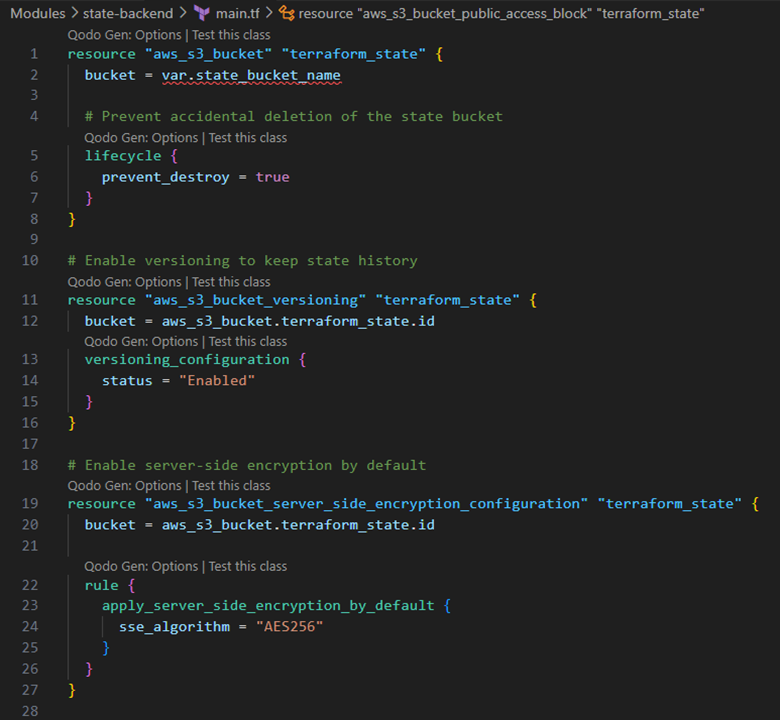
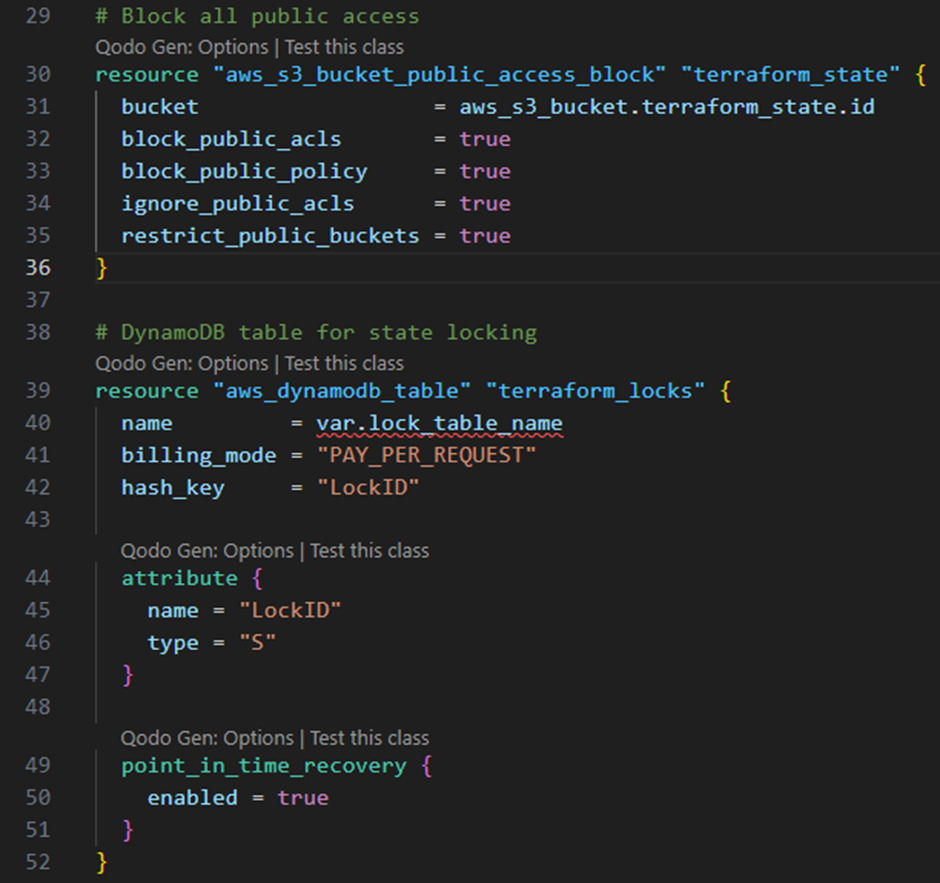
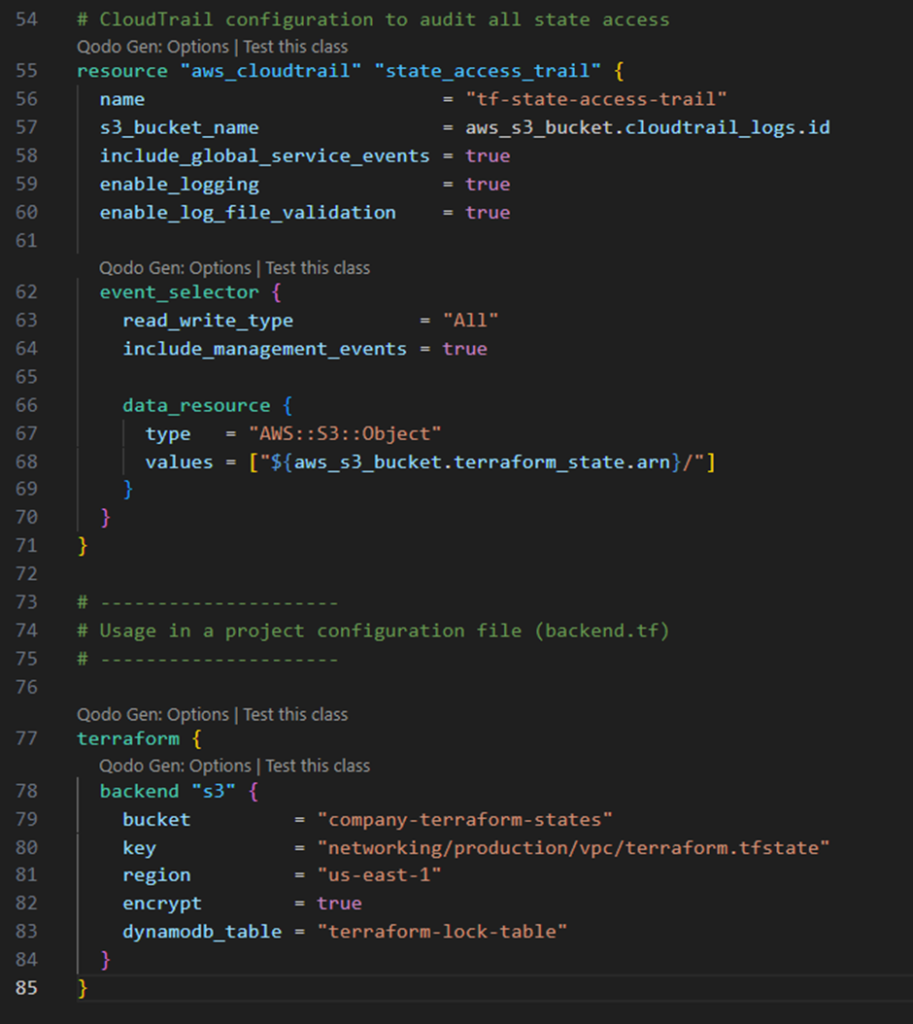
This example demonstrates several advanced state management practices. First, it implements defence-in-depth security with multiple protective layers: server-side encryption, complete public access blocking, and versioning for historical integrity. Furthermore, the configuration includes CloudTrail auditing specifically for state access operations, by creating an immutable record of who accessed or modified state files.
The most sophisticated aspect is the structured state path naming convention, which implements a consistent schema for state file organization. This hierarchical structure enables granular access controls and makes state files discoverable for teams working across multiple infrastructure components.
Going beyond just the technical implementation, mature organizations develop operational procedures around state management. They implement automated state validation processes that detect corruption or tampering, establish clear workflows for state migration during refactoring, and maintain documentation about state file dependencies across infrastructure components. By elevating state management from a technical detail to a critical governance concern, organizations can maintain infrastructure reliability even as their IaC implementations grow in complexity and scale.
Conclusion
The advanced practices outlined in this guide – modular infrastructure design, automated testing, and state management – represent the cornerstone of enterprise-grade Infrastructure as Code implementations. By organizing infrastructure into hierarchical modules with clear interfaces, teams can build maintainable, reusable components that evolve independently. Comprehensive testing frameworks that validate both resource configuration and functional requirements ensure reliability while maintaining development velocity. Sophisticated state management approaches with segmentation, encryption, and structured access controls provide the governance foundation necessary for collaborative infrastructure development.
As we conclude this four-part journey through Infrastructure as Code, it’s clear that IaC has transformed from a simple automation tool into a comprehensive discipline that shapes modern infrastructure management. From the foundational concepts introduced in our first instalment to these advanced practices, the evolution of IaC mirrors the maturation of cloud infrastructure itself. Organizations that embrace these principles can achieve the seemingly contradictory goals of increasing deployment velocity while enhancing reliability and security.
The future of infrastructure management lies not just in automation, but in treating infrastructure as a true software discipline – with modular design patterns, rigorous testing, and structured collaboration workflows. By implementing the practices outlined across this series, organizations can build infrastructure platforms that scale with their business needs while maintaining the governance required in today’s complex regulatory environment.
Back to Part 1: Infrastructure as Code (IaC): A Guide to Modern Infrastructure Management
WRITTEN BY
Ulrich Van Rooyen